Checkpoint Firewall Tutorial Pdf
The Firewall Configuration Guide provides information about how to configure supported firewalls proxy servers and security devices to work with Security Reporting Center. The Firewall lets system administrators securely control access to computers clients servers and applications.
Intro Checkpoint Firewall Cloud Computing Computer Security
Firewall Getting Started Guide.
Checkpoint firewall tutorial pdf. Book at Checkpoint Saint Petersburg. What command lists the firewall kernel modules on a Security Gateway. Adding Users to the Security Policy.
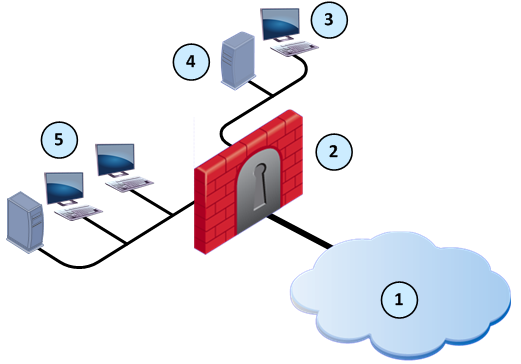
A primary goal of a firewall is to control access and traffic to and from the internal and external networks. Join Millions of Learners From Around The World Already Learning On Udemy. Remote Access to the Network.
This document is designed for on-screen reading. Checkpoint SmartConsole Adding Rules in Firewalls Adding NAT rules in Firewall Policy package Network Monitoring 19. Book at Checkpoint Saint Petersburg.
Start Today and Become an Expert in Days. What flag options you would use to dump the complete table in a user-friendly format assuming the connections in the table are more than 100. Firewalls are typically implemented on the network perimeter and function by defining trusted and untrusted zones.
Most firewalls will permit traffic from the trusted zone to the untrusted. Checkpoint Firewall R7730 Pdf Checkpoint Firewall Tutorial The Firewall Configuration Guide provides information about how to configure supported firewalls proxy servers and security devices to work with Security Reporting Center. Join Millions of Learners From Around The World Already Learning On Udemy.
Checkpoint Firewall Presentation - Free download as Powerpoint Presentation ppt PDF File pdf Text File txt or view presentation slides online. Hiew tutorial hexadecimal editor part 6 check point firewall-1 vpn-1 check point edge websense installation guide supplement for integrated check point. Important Commands Cpinfo show tech-support Cisco Set interface eth0 ipv4 address192168101 subnet-mask 2552552550 Show interfaces all Fw stat Fw unloadlocal Fw monitor 20.
What command would give you a summary of all the tables available to the firewall kernel. Packet Filtering Stateful Inspection Application Intelligence Security Gateway Inspection Architecture INSPECT Engine Packet Flow DeploymentConsiderations Standalone Deployment Distributed Deployment Standalone Full HA. Ad Learn Firewall Online At Your Own Pace.
Check Point Tutorials Contents. Sun 15 dec 2013 235400 gmt checkpoint firewall tutorials pdf - to get started with your self-study we recommend that you become familiar with the check point firewall interview questions - download as word doc doc docx pdf file pdf text file. Allow Remote Root Access Vmware ESX 4.
And there are few GUI compounds. Ad Best Price Guarantee. The Firewall Rule Base defines the quality of the access control and network performance.
- Introduction to Firewalls - Firewall Basics Traditionally a firewall is defined as any device or software used to filter or control the flow of traffic. This guide is designed for on-screen reading. Firewall R77 Versions Administration Guide.
Managing Network Access Control. Ad Learn Firewall Online At Your Own Pace. The Check Point Firewall OSI Model Mechanism for controlling Network traffic.
Ad Best Price Guarantee. The checkpoint firewall has few ideas basics of checkpoint firewall architecture there are diverse operating systems and models for the checkpoint firewall. Start Today and Become an Expert in Days.
Chapter 1 FireWall-1 Access Control The Need for Access Control 9 FireWall-1 Solution for Secure Access Control 9 Access Control at the Network Boundary 10 The Security Rule Base 11 Example Access Control Rule 11 Rule Base Elements 12 Implied Rules 12 Preventing IP Spoofing 13 New Services 15 Considerations for Access Control 17 Spoof Protection 17. Check Point Firewall Security Solution. You will learn about the security and NAT regulations and also about troubleshooting problems.
Installing VMware ESX 4.
Check Point Firewall Security Solution
Intro Checkpoint Firewall Cloud Computing Computer Security
Intro Checkpoint Firewall Cloud Computing Computer Security